IoT VPC Network Pricing: Data Transfer & Security Explained!
Are you wrestling with the complexities of Internet of Things (IoT) Virtual Private Cloud (VPC) network pricing? Understanding these intricacies is no longer a luxury, but a necessity in today's interconnected world.
The digital tide has turned, and the Internet of Things (IoT) has become a relentless current, sweeping through every facet of our lives. From smart homes to intelligent infrastructure, the proliferation of connected devices is reshaping industries and redefining how we interact with the world. But this explosion of connectivity comes with a crucial caveat: security. The vast amounts of data generated by these devices, and the critical functions they control, make them prime targets for malicious actors. This is where the Virtual Private Cloud (VPC) steps in, offering a haven of security in the otherwise turbulent seas of the internet. The challenge, however, lies in navigating the often-complex world of pricing associated with these essential network environments. Consider the scenario: each month, you transmit a substantial 2 tebibytes (TiB) of data through a secure tunnel, moving data from your virtual private cloud (VPC) network to your data center. Simultaneously, another 2 TiB flows in the opposite direction, a two-way exchange essential for the operation of your IoT ecosystem. Furthermore, you're utilizing a reserved external IP address, a critical component for accessibility. But how does all of this translate into cost? And more importantly, how can you optimize your setup to ensure both security and affordability?
Let's delve into a specific, yet common, scenario. Imagine an IoT service provider, based in a hypothetical city, let's say, "Veridia," a bustling hub for technological innovation. This provider offers smart building solutions, managing everything from climate control to security systems for commercial properties. They're utilizing an Amazon Web Services (AWS) VPC to secure their IoT infrastructure. Each month, as in the general case described earlier, they transfer 2 TiB of data from their VPC to their central data center, and another 2 TiB in the opposite direction. Their gateway utilizes a reserved external IP address to allow for secure, remote access to their managed devices. The cost implications of this seemingly straightforward setup are significant. They need to understand the cost of data transfer (inbound and outbound), the cost of the reserved IP address, and any potential charges for the VPC itself and related services.
Before we proceed, let's establish a firm understanding. An IoT VPC is, at its core, a private cloud environment. It's specifically architected for IoT applications, offering a crucial layer of isolation. This isolation is the cornerstone of both data privacy and security, creating a walled garden for your IoT devices. Consider it a virtual fortress, shielding your sensitive data from unauthorized access. In this isolated network, IoT devices can communicate securely, exchanging data without exposing themselves to the broader internet's inherent vulnerabilities. This is particularly critical for applications that handle sensitive information, such as patient data from medical devices, or financial transactions from smart payment systems. By placing these devices within an IoT VPC, you're effectively minimizing the attack surface, reducing the risk of data breaches, and ensuring compliance with regulations like HIPAA or GDPR.
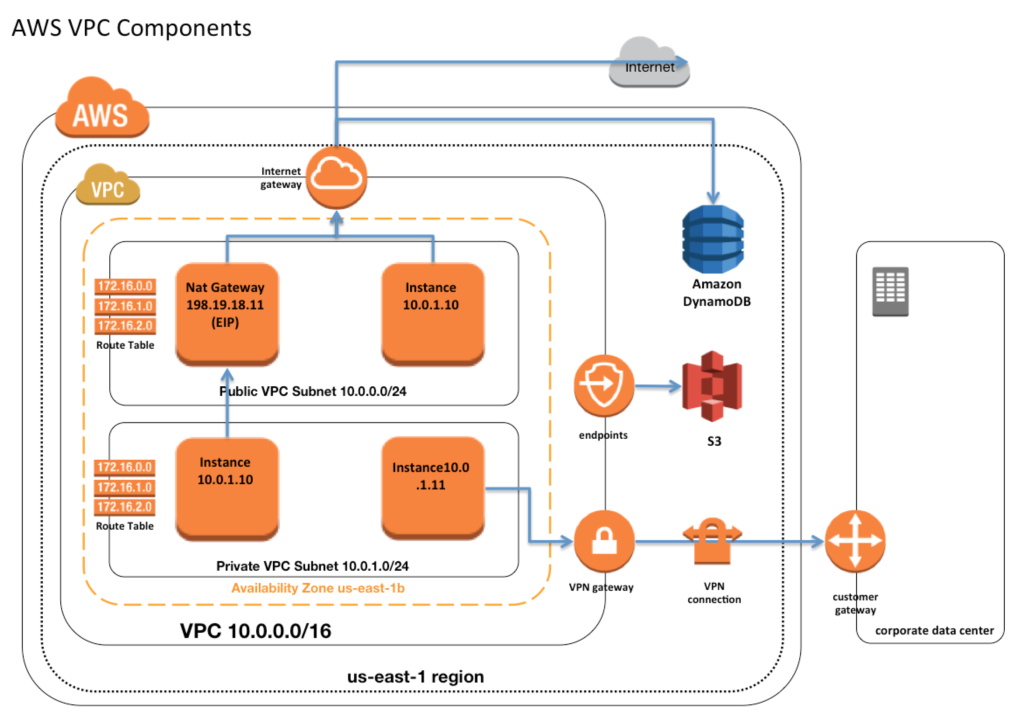
The journey towards securing your IoT infrastructure within a VPC begins with its creation. You'll initiate this process on your chosen cloud providerAWS, Google Cloud Platform (GCP), or Microsoft Azure, for example. The subsequent steps involve meticulously defining subnets, security groups, and route tables. Subnets segment your VPC into logical divisions, allowing you to organize your resources and control network traffic more precisely. Security groups act as virtual firewalls, governing the inbound and outbound traffic for your resources, and providing another layer of defense. Route tables dictate the paths that network traffic takes, ensuring that data flows correctly between your subnets and external networks. The careful configuration of these elements is critical to building a secure and efficient VPC.
Creating a VPC on a cloud platform like AWS involves a series of steps, typically managed through the AWS Management Console, the AWS Command Line Interface (CLI), or infrastructure-as-code tools like Terraform. You'll begin by specifying the CIDR block for your VPC, which defines the IP address range for your network. Next, you'll create subnets within your VPC, each residing in a specific Availability Zone within a region. Availability Zones are isolated locations designed to ensure high availability; even if one zone experiences an outage, your resources in other zones remain operational. Then, you'll configure security groups, defining the rules that govern traffic flow, specifying which ports and protocols are allowed or denied. Finally, you'll configure route tables to direct traffic to the appropriate destinations, such as the internet gateway or a virtual private gateway for connecting to your on-premises network.
The beauty of VPCs lies in their adaptability. They can be tailored to fit a wide range of IoT applications, from smart thermostats in your home to complex industrial IoT deployments. For example, a company managing a fleet of autonomous vehicles would need a highly secure VPC to handle the constant stream of data from these vehicles, including real-time sensor data, location information, and control commands. A healthcare provider deploying remote patient monitoring devices would similarly utilize a VPC to ensure the privacy of patient data, adhering to strict compliance regulations. Even at the simplest level, the use of a VPC for a home automation system, allows for the segregation of your IoT devices, and can enhance security and improve performance. The scalability and flexibility of VPCs enable them to meet the evolving needs of IoT projects of any size or complexity.
The concept of ingress data transfer to VPCs is, typically, free. Cloud providers often don't charge for data entering your VPC. This is a strategic move, as it encourages the adoption of their services and makes it easier for you to get data into your secure environment. However, this doesn't mean that all data transfer is free. It's essential to pay close attention to the charges associated with outbound data transferthe data leaving your VPC and going to the internet, or to other cloud services. These outbound charges can quickly accumulate, and it's crucial to optimize your network configuration to minimize these costs. This can involve using services like content delivery networks (CDNs) to cache frequently accessed data, thereby reducing the amount of data that needs to be transferred from your VPC. Efficiently designed architecture combined with careful monitoring of outbound data usage can help to keep your costs under control.
Within your VPC, setting up security groups and Network Access Control Lists (ACLs) on your elastic network interfaces is another vital step. Security groups act as a first line of defense, controlling the inbound and outbound traffic at the instance level. They act as virtual firewalls, allowing or denying traffic based on specified rules. Network ACLs provide an additional layer of security at the subnet level, enabling you to control traffic flow across multiple instances within a subnet. The combination of these security measures allows you to create a highly secure network environment.
Furthermore, utilizing VPC endpoint conditions to control access to AWS IoT Core data over VPC endpoints is a strategic move to enhance security. VPC endpoints allow you to privately connect your VPC to supported AWS services, without using public IP addresses or traversing the internet. This means that your IoT devices can securely communicate with AWS IoT Core, using a private network connection. By implementing VPC endpoint conditions, you can further control access to your IoT data, restricting which devices or users can access the service through the endpoint. The correct combination of security measures will drastically reduce your potential attack surface.
Let's return to our IoT service provider in Veridia. The company needs to understand the implications of data transfer costs. While ingress data is free, every byte leaving the VPC is subject to charges, especially if the data travels to the internet. If the service provider is transmitting 2 TiB of data outbound each month, this could result in substantial charges, depending on the cloud provider's pricing structure. Their strategic advantage lies in carefully monitoring and optimizing this data flow, and carefully considering data storage, data transfer, and IP address use costs to fully optimize their resources.
For our Veridia-based service provider, a further optimization strategy would be to carefully consider the use of AWS IoT Core data VPC endpoints. These endpoints allow their IoT devices to connect directly to AWS IoT Core via a private network connection within their VPC, bypassing the public internet. The benefit is two-fold: increased security and potential cost savings. The security gains are immediately obvious: reducing the attack surface and ensuring data privacy. The cost savings are possible by reducing the amount of data transfer over the public internet, which often has higher associated costs.
In conclusion, understanding the intricacies of IoT VPC network pricing is no longer a matter of simply configuring your network. It's a critical element of overall cost management and security. The key lies in carefully designing your architecture, being mindful of the data transfer costs (especially outbound), implementing security best practices, and regularly monitoring and optimizing your network configuration. From the smart buildings of Veridia to the far corners of the IoT landscape, these principles remain constant. In a world where data is the lifeblood of innovation, protecting its flow, and understanding its cost, is paramount. By embracing these principles, you can ensure that your IoT deployments are not only secure and efficient, but also economically sustainable, providing you with the agility and resilience you need to thrive in the ever-evolving landscape of the Internet of Things.

Affordable IoT VPC Networks A Guide To Pricing And Optimization
Affordable IoT VPC Networks A Guide To Pricing And Optimization
What Is VPC in AWS? 1Byte1Byte